News
Study: Device Companion Apps Expose IoT Security Vulnerabilities
Academicians published a study of Internet of Things (IoT) security, finding that companion apps to connected devices can expose vulnerability attack vectors.
The study -- conducted by researchers from Federal University of Pernambuco, Brazil, and the University of Michigan -- decided to investigate IoT device security by analyzing companion apps used to manage devices, instead of the devices' firmware binaries, which can be difficult to access and analyze. Thus the resulting report is titled "Beware of the App! On the Vulnerability Surface of Smart Devices through their Companion Apps."
"A key finding of this study is that the communication between an IoT device and its app is often not properly encrypted and authenticated and these issues enable the construction of exploits to remotely control the devices," the report said.
The research involved the creation of exploits to attack five popular IoT devices. "We were successful in creating exploits for all five devices and able to control them, leveraging information that we gathered while analyzing the companion apps, both statically, through program analysis, and dynamically, through monitoring the network, the report said.
That five-device attack research was conducted along with a larger study that found analyzing 96 popular IoT devices only required analyzing 32 companion apps.
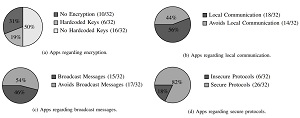 [Click on image for larger view.]
Distributions of Different Features for the Set of Analyzed Apps
[Click on image for larger view.]
Distributions of Different Features for the Set of Analyzed Apps
(source: Federal University of Pernambuco, Brazil, and the University of Michigan)
"Among the conservative findings, 50 percent of the apps corresponding to 38 percent of the devices did not use proper encryption techniques to secure device to companion app communication," the paper said.
In focusing on the communication between a smartphone app and the device it connects to, researchers said any flaws in the protocols being used could allow for a wide range of attacks in which the bad guys could take over complete control of a device.
Finally, in discussing defense strategies, the researchers focused on proper key management, having found a plethora of hard-coded or unencrypted keys. The paper discusses different strategies to ensure key safety. It also listed one particular strategy that probably wouldn't be so effective: "Code obfuscation is unlikely to be an adequate defense."
About the Author
David Ramel is an editor and writer at Converge 360.